Using Single Sign-On (SSO) in CDMS
Table of Contents
SSO for users
Logging in to Castor CDMS
When your institution requires SSO, you will be unable to log in with the Castor CDMS credentials you previously set. Instead, after entering your email address on the login page, you will be redirected to your institution's Identity Provider (IdP) to log in.
Log in using Castor CDMS credentials
You will be prompted to enter your Castor CDMS password if your institution does not enforce SSO or has exempted your account from using SSO. You can read more about logging in to Castor CDMS on this helpdesk page.

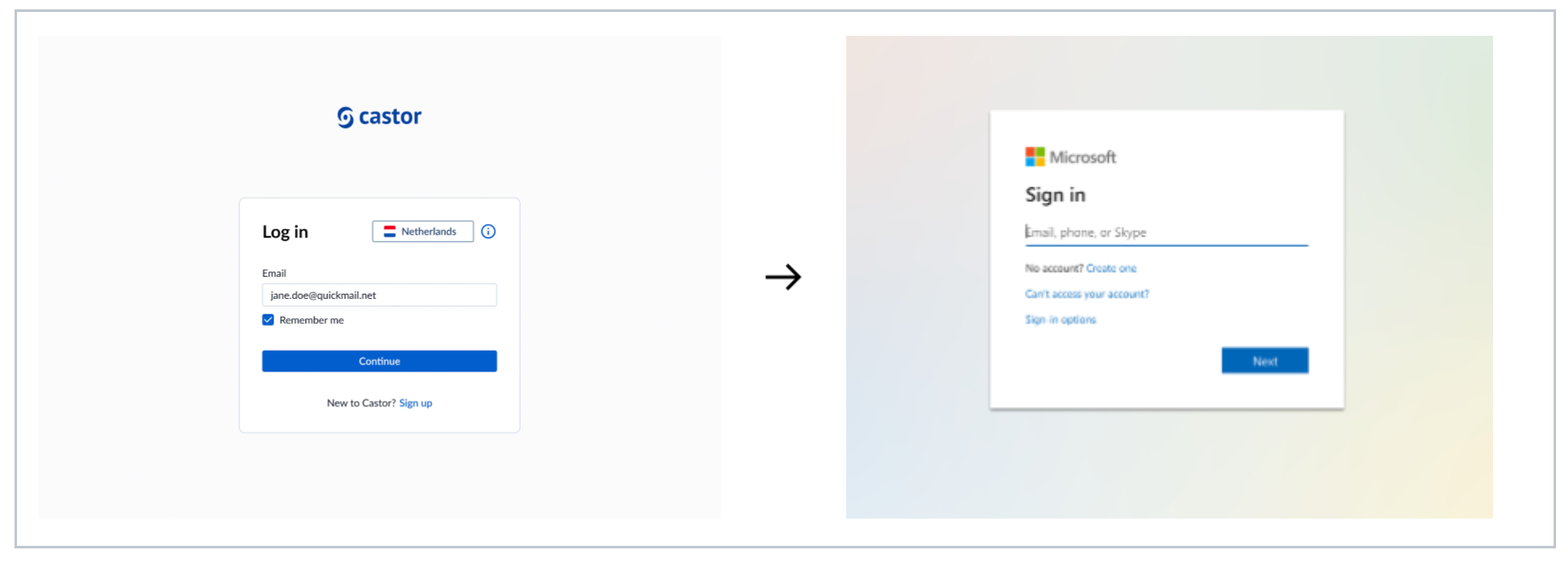
Log in using SSO
You will be redirected to your organization's IdP (for example, Azure AD) if your institution enforces SSO.
Inviting users to a study
The process of inviting users to a study is the same for SSO users and non-SSO users. More information about inviting users can be found on this page.
Using the API
For security reasons, we require SSO users to login to Castor CDMS using their Identity Provider on a regular basis. After 7 days of inactivity, you must log in again through the user interface before you can generate a new OAuth token.
If you have not logged in to the system for more than 7 days, the /oauth/token endpoint will return the following error: “For security reasons, we require SSO users to login to Castor CDMS using their Identity Provider on a regular basis. You have not accessed the system in 7 days. Before making any API calls, please log in via the user interface.”
It is possible to make an exception to SSO enforcement on a user account level. Please contact the department or person responsible for managing Castor CDMS in your institute to do so.
SSO for institutes
SSO allows users to access multiple web applications using a single set of login credentials. By providing a single point of authentication and authorization, SSO enables your institution or site to gain centralized control over user access and management. This can help you gain a better handle on the compliance, security, and data governance of their research data. Furthermore, SSO can improve the user experience by allowing researchers, staff, and other users to log in to Castor CDMS using their existing institutional credentials rather than remembering and managing multiple sets of login information.
Supported protocols
Castor supports the SAML and OIDC protocols for SSO authentication. We only onboard new customers on the OIDC protocol.
SAML SSO flows
For customers using SAML-based SSO, both the Service Provider (SP) and Identity Provider (IdP) initiated flows are supported.
Enforcing SSO
As an institution, you can enforce the use of SSO for your email domain (for example, hospital.com). Your email domain will be associated with an IdP (for example, Azure AD), which can be used to log in to the application.
Implications
Enforcing SSO has a number of implications. Users with your email domain:
- … will be redirected to an IdP in order to authenticate themselves or will directly use the IdP to get access to Castor CDMS.
- They will use the login page and credentials from their IdP.
- … cannot log in using their Castor CDMS credentials anymore.
- Instead, they will be redirected, as described above.
- … cannot use Castor CDMS’ 2 Factor Authentication (2FA) anymore.
- Instead, they will use the 2FA of the IdP, if applicable.
- … must log in using the IdP every 7 days in order to maintain access to the API.
- SSO cannot be used to manage API credentials. To maintain access to the API, we require users to log in every 7 days for security reasons. It is not possible to generate a new OAuth token after 7 days of inactivity, and users must first log in using the IdP to regain access.
Exceptions
It is possible to make exceptions to the SSO enforcement on a user account level. Such an exception enables the user to log in using their Castor CDMS credentials instead. Exceptions can be made for:
- Regular users (i.e., user accounts that use a shared email box and cannot login through SSO)
- System users (i.e., user accounts that are not used by an ‘actual’ user, but used for API integrations)
To make such an exception, contact a member of the customer success team. Please include the email address of the user account in your request, as well as a description of whether this concerns a regular user or a system user.